Debunking Misconceptions About Direct Email Marketing to UHNWIs: An Interdisciplinary Analysis
In this article, we aim to analyze persistent misconceptions surrounding Direct Email Marketing (DEM) targeted at Ultra-High-Net-Worth Individuals (UHNWI) and provide an evidence-based perspective on its effectiveness. By integrating insights from data science and cognitive psychology, we examine the mechanisms that drive engagement and debunk the myths that hinder success in this specialized marketing domain.
Context for Evaluation
Since 2007, UHNWI Data has specialized in delivering digital content for clients by leveraging expertise in wealth intelligence and data science. Over the years, our organization has conducted over 700+ campaigns, delivering millions of emails to UHNWI, achieving response rates that consistently exceed industry benchmarks for elite audiences.
This extensive experience, coupled with qualitative insights from discussions with hundreds marketing executives and quantitative analyses of campaign performance, allows us to identify and address the most persistent myths and misconceptions in the field. These findings are further informed by theoretical frameworks in behavioral psychology and information processing.
To provide a comprehensive perspective, we analyze four key myths about DEM that often mislead practitioners and explore how advanced analytical methods and psychological theories can guide more effective strategies.
Myth #1: “Billionaires Don’t Read Emails”
One of the most common beliefs is that billionaires are inaccessible via email. This notion often stems from anecdotal experiences and lacks empirical validation. Cognitive psychology and data science provide valuable insights to refute this claim.
The Data Speaks
Our database comprises 80% of the global billionaire population, each of whom receives tailored, relevant messages. Over the past decade, we’ve observed:
Hundreds of direct responses from billionaires, including rejections, requests for information, and engagement inquiries.
Clear evidence of interaction with tailored content designed to address the specific interests and needs of this audience.
This aligns with selective attention theory (Broadbent, 1958), which posits that individuals prioritize information perceived as valuable or relevant to their objectives. In this case, carefully curated content penetrates the cognitive filters of UHNWI.
Critical Success Factors
The effectiveness of DEM relies on several key parameters:
Database Size: A statistically significant sample size is critical. For instance, a list of 100 UHNWI contacts is unlikely to yield substantial results. However, campaigns targeting 2,000 billionaires plus 1500+ centi-millionaires demonstrate markedly higher response rates.
Content Relevance: Messages must be highly personalized, reflecting the recipient’s professional profile, interests, and priorities.
Timing and Consistency: Even highly relevant emails may be overlooked if sent at an inopportune moment. Long-term campaigns, spanning 12+ months, significantly increase the likelihood of engagement.
Examples of Interaction
Based on an in-depth analysis of our long-term clients who maintain exclusive agreements with us, particularly those in the aviation industry, we can state with a significant degree of certainty that we are capable of consistently delivering stable results. Specifically, we can achieve at least one sale per year for our clients, with each transaction carrying an eight-figure price tag. This track record demonstrates our ability to navigate niche markets and maintain high-value outcomes tailored to the unique needs of our clients.
Conclusion
The assumption that billionaires don’t read emails arises from insufficient sample sizes, irrelevant content, and unrealistic expectations of immediate results. By addressing these shortcomings, DEM can achieve measurable success within this exclusive demographic.
Myth #2: “Short Emails Are More Effective for UHNWI”
Another widespread misconception is that concise emails with minimal content are more effective. While brevity is often praised in marketing, research suggests that this approach oversimplifies the needs of UHNWI, who rely on rich and detailed information for decision-making.
The Dynamics of Information Processing
Successful individuals process large volumes of information daily. To manage this cognitive load, they employ efficient scanning mechanisms that prioritize “keywords” or standout elements within incoming messages. However, oversimplified emails often fail to provide enough context to trigger active attention.
What Constitutes a ‘Keyword’?
In this context, a “keyword” is not limited to a single word or phrase. It can also include visual elements, such as static or animated graphics, that capture the recipient’s attention.
How Scanning Works
Cognitive psychology research illustrates the scanning process:
Scanning Phase: [irrelevant words] → [irrelevant words] → [irrelevant words] → [KEYWORD] → STOP → ACTIVE ATTENTION TRIGGERED → EXPAND AND READ (Figure 3.)
Engagement Phase: If a “keyword” is detected, the recipient’s attention shifts to detailed analysis of the message.
Without sufficient content, the scanning process terminates prematurely, and the email is dismissed.
[irrelevant words] → [irrelevant words] → [irrelevant words] → OUT
Content Volume and Relevance
For UHNWI, the likelihood of engagement increases with:
Comprehensive content that addresses potential questions or concerns.
Visual and textual elements designed to capture and sustain attention.
Sparse content risks creating the impression of low effort or irrelevance, leading to deletion without further consideration.
Examples of Content Depth
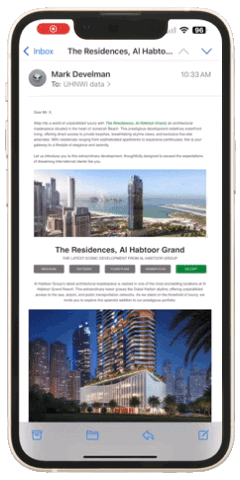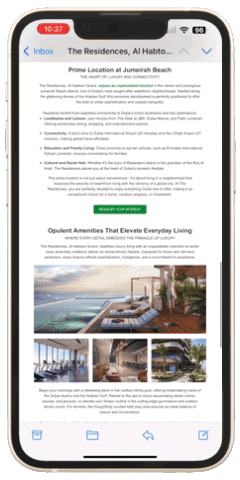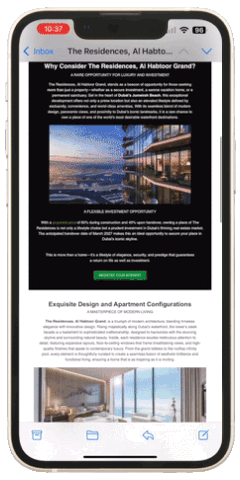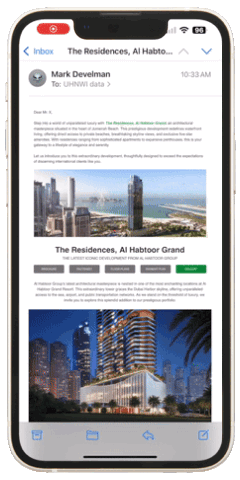
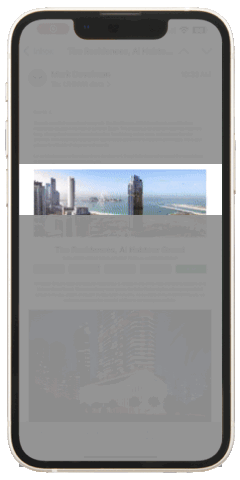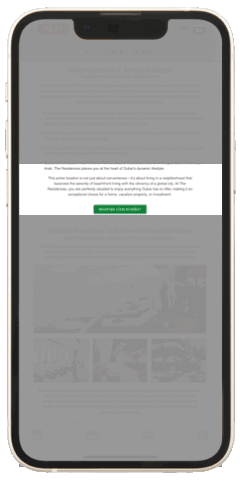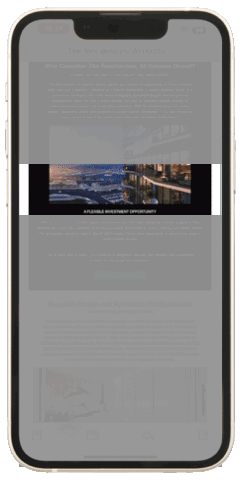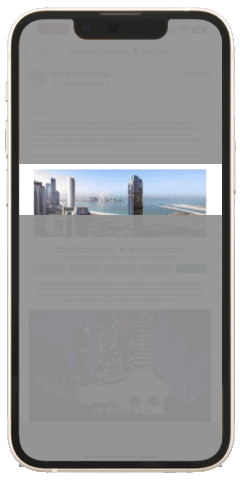
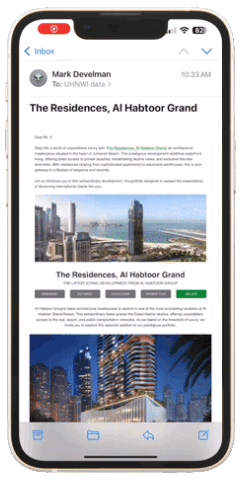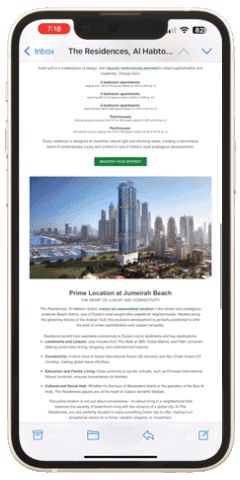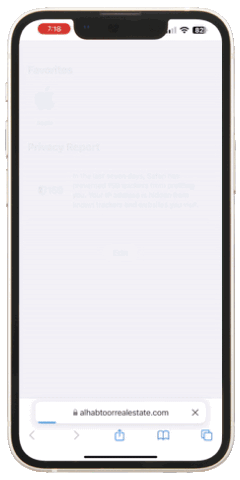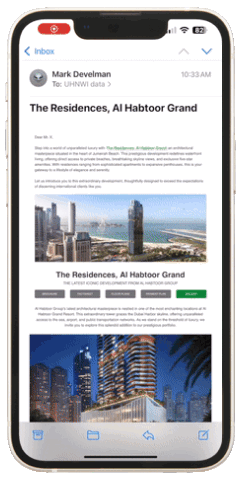
Emails that include tailored case studies or detailed infographics about investment opportunities consistently outperform generic, brief messages. For example, the campaign below targeting real estate investors included visual elements such as detailed images, videos, 3D tours, downloadable brochures, floor plans, and other relevant information. These elements usually lead to meaningful interactions if we reach the right individual at the right moment.
Do you think the information provided is perceived exactly as you see it. (Figure 1 represents an example of a real estate campaign with a moderate amount of information displayed)? Unfortunately, it is not! The window for capturing active attention in unsolicited emails is exceptionally narrow. Even with a comprehensive set of information, the recipient may process only a small portion during their initial scan. (Figure 2 represents an example of a bottleneck explained by selective attention theory).
If, as shown in Figure 2, the recipient does not detect the ‘KEYWORD,’ the narrow window of their active attention still processes fragmented information. Now, let’s analyze the amount of information required for decision-making. If the information presented in the presentation has been thoroughly studied, it should be sufficient to prompt one of the following decisions: interested → request more information, not interested → delete, not interested → unsubscribe, not interested → reply indicating disinterest, and so on.
Thus, the primary goal is to create the broadest yet most relevant set of information about your offer, maximizing the chances of detecting the ‘KEYWORD.’ This, in turn, activates active attention. A message containing minimal or insufficient information is generally not effective.
This illustration demonstrates that scrolling through content, regardless of its length, typically takes only a few seconds. As such, the notion that a longer message automatically worsens content perception is not entirely accurate. However, if the recipient does not detect the ‘KEYWORD’ within these few seconds, they are likely to stop engaging with the message. On the other hand, detecting the ‘KEYWORD’ prompts the recipient to pause, activating ACTIVE ATTENTION. This leads them to explore the information more thoroughly, as illustrated in Figure 3 which represents an example of viewer engagement based on triggered active attention..
Conclusion
The belief that shorter emails are inherently better is a misinterpretation of marketing best practices. Rich, detailed emails aligned with the cognitive preferences of UHNWI are far more effective at driving engagement.
Myth #3: “Regulations Make Direct Email Marketing to UHNWI Impossible”
One of the most prevalent misconceptions surrounding Direct Email Marketing (DEM) is the incorrect classification of this communication method. With the tightening of regulations like the General Data Protection Regulation (GDPR), many assume that sending unsolicited emails is inherently illegal. This oversimplified interpretation often leads to abandoning effective communication strategies out of fear of potential legal consequences.
To dispel this myth, it’s essential to examine the situation in greater detail. At the heart of this misunderstanding lies a legal and logical paradox: how can one obtain prior consent for communication if any initial contact is theoretically “illegal”? This paradox is especially relevant in the context of modern data protection laws, such as GDPR.
The Legal Paradox of First Contact
• The Core Issue: Legal communication requires prior consent, yet obtaining that consent necessitates initial contact.
• The Key Question: If the first contact is already considered a violation, how can a dialogue even be initiated?
This paradox undeniably exists, but most regulatory frameworks provide exceptions or legitimate grounds for first contact. Without these exceptions, the entire system of professional communication would collapse.
GDPR and similar regulations address this issue through exceptions, such as legitimate interest.
Legitimate Grounds for First Contact
1. Legitimate Interest:
Communicating relevant products or services based on the recipient’s professional profile.
Sharing valuable market insights or initiating collaboration discussions.
2. Personalization and Transparency:
Messages must be tailored to individual recipients.
Clear disclaimers should explain the purpose of the contact and provide opt-out options.
3. Moderation:
Avoid overwhelming recipients with frequent messages. A cadence of no more than one email per month is recommended.
Example Disclaimer:
“We are contacting you because we believe our offer may be relevant and beneficial based on your professional profile. If this is not the case, please let us know, and we will immediately cease further communication. In the absence of an opt-out request, we reserve the right to send relevant updates no more than once a month. This email was sent manually and is not part of any mass-mailing campaign.”
Conclusion
Direct Email Marketing to UHNWI is not inherently at odds with data protection regulations. By adhering to principles of transparency, personalization, and moderation, it is possible to engage ethically and effectively.
Myth #4: “Obtaining Personal Information for Direct Email Marketing Is Illegal”
The legality and ethics of acquiring personal contact information often deter organizations from pursuing DEM. To address this concern, it is essential to differentiate between methods of data acquisition.
Ethical Data Collection
Illegally Obtained Databases: These include data acquired through system breaches, hacking, or leaks. Using such databases is unequivocally illegal and unethical, with severe legal consequences.
Data from Brokers: Personal information acquired from data brokers often exploits gaps or ambiguities in user agreements on digital platforms. While technically legal, this method raises significant ethical concerns. If your business promises data security and confidentiality to clients, using such data contradicts these principles and may damage your reputation.
Research-Based Methods: Personal information collected through in-depth research and internal analytics is entirely legal and ethically acceptable. This involves analyzing publicly available information, such as names, domains, and corporate affiliations, to identify potential email patterns.
Ethical Data Collection Through Research
The third method is the approach we advocate and employ. We neither purchase nor steal personal data, and we encourage others to uphold these same ethical standards. Our process involves:
Publicly Available Information: By leveraging publicly accessible data, such as a person’s name, affiliated companies, and their associated domain names you can legally deduce potential email formats. This process treats email addresses as the product of analytical efforts rather than private, inaccessible data.
Pattern Identification: Email patterns (e.g., first.last@company.com) are often easily discernible based on corporate standards. Once patterns are identified, you can generate likely email addresses for further verification.
Verification Through Non-Commercial Messaging: To validate these addresses, send an initial message that is personalized, respectful, and non-commercial. This message should focus on expressing personal admiration or gratitude without any promotional intent.
Example Initial Email:
Subject: Admiration for Your Work
Dear Mr. X,
I hope this message finds you well.
I have long admired your remarkable achievements and the substantial impact your work has had in [specific area, e.g., philanthropy, technology, etc.]. Your initiatives are truly inspiring and have motivated countless individuals, myself included, to think bigger and strive for meaningful change.
For some time, I have wanted to express my sincere appreciation but was uncertain about the best way to reach you. Based on standard corporate email conventions, I deduced this address and truly hope this message reaches you in good spirits and does not cause any inconvenience.
If this email is unwelcome or inappropriate, please accept my apologies. Should you prefer not to receive further communication from me, I would be grateful if you could kindly let me know.
Thank you for your time, and I wish you continued success in all your endeavors.
With the utmost respect and best regards,
[Your Full Name]
[Your Contact Information, optional: e.g., phone number]
Ensuring Accuracy and Reliability
To further validate email addresses:
Monitor Bounced Emails: Proper DNS configuration enables detailed feedback on undeliverable emails. Addresses that do not return as “bounced” within 48 hours can be flagged for further analysis.
Confirm Activity: Conduct subsequent rounds of verification to ensure the email is active and monitored by the recipient.
This process may take time, but if executed with patience and precision, it can yield reliable results without appearing intrusive or unprofessional.
Avoiding Automation Pitfalls
In today’s regulatory and cybersecurity landscape, reliance on automated tools or browser extensions for email tracking has become increasingly unreliable. Ultra-High-Net-Worth Individuals (UHNWI) often employ robust cybersecurity measures, including:
Advanced email scanning systems that simulate email opens and link clicks as part of security protocols.
Corporate and private email servers designed to filter suspicious activity before emails reach the inbox.
As a result, the activity you observe, such as email opens or link clicks may not reflect genuine user behavior. This makes traditional tracking methods unreliable and undermines the accuracy of engagement metrics.
The only truly reliable confirmation of an email’s validity is a direct response from the recipient, regardless of its content. Until such a response is received, the email address should be considered partially verified.
Navigating the Balance Between Persistence and Intrusiveness
When recipients fail to respond, it is essential to tread carefully to avoid being perceived as intrusive while maintaining a respectful form of persistence.
Intrusiveness:
Intrusiveness occurs when you continue contacting someone against their explicitly stated wishes, either directly (e.g., “stop emailing me”) or indirectly (e.g., ignoring multiple messages).
However, if the recipient never receives your emails due to spam filters or an overflow of incoming correspondence, you cannot technically be considered intrusive, as your intent remains genuine and respectful.
Ignoring Signals:
If emails are delivered and read but no response is received, this could indicate a lack of interest.
However, silence should not automatically be interpreted as a clear rejection unless explicitly communicated.
By crafting respectful, non-commercial messages that provide value and offering clear opt-out options, you minimize the risk of being labeled intrusive.
Ethical Legitimacy of Research-Based Email Discovery
Is it ethical and legal to use publicly available information to deduce email addresses, verify them through non-commercial communication, and subsequently protect this data responsibly? Yes, provided the following criteria are met:
Transparency: Clearly disclose how the email address was identified.
Non-Commercial Intent: Ensure initial communication focuses on building a personal connection rather than promoting products or services. By effectively using a sequence of messages with well-crafted disclaimers, you set the stage for presenting commercial content.
Data Protection: Safeguard collected data in accordance with applicable privacy laws.
Conclusion
Obtaining personal contact information for Direct Email Marketing can be done ethically and legally through research-based methods. By leveraging publicly available data, carefully verifying email addresses, and maintaining respectful communication, you can establish a legitimate foundation for engagement with your target audience.
Respect, transparency, and moderation are the cornerstones of this approach, ensuring compliance with data protection regulations while fostering trust with recipients.
In Conclusion: The Statistical Reality of DEM
Direct Email Marketing is a long-term strategy requiring patience, consistency, and a data-driven approach. Success hinges on statistical principles, not immediate gratification. For campaigns targeting UHNWI, a minimum horizon of 12 months is essential to generate meaningful results.
If after this period no engagement is observed, the issue likely lies in the product offering, pricing strategy, or communication approach—not the method of DEM itself. Numerous successful case studies confirm that, when executed correctly, DEM is a highly effective tool for reaching UHNWI.
At UHNWI Data, we specialize in crafting tailored, compliant strategies to help businesses connect with this exclusive audience. Contact us today to learn how our expertise can transform your outreach efforts.